Zero-Knowledge Proofs
Department of Electrical Engineering, IIT Bombay
November 6, 2024
Zero-Knowledge Proofs
Interactive protocols that allow a prover to prove the validity of a statement without revealing anything else
Traditional proofs have no interaction
- Sequence of statements each of which is an axiom or follows from axioms via derivation
Examples of statements
- Two graphs G_1, G_2 are not isomorphic
- x \in \mathcal{QR}_N for a composite N
Information
- In information theory, entropy is used to quantify information
- Entropy of a discrete random variable X defined over an alphabet \mathcal{X} is \begin{equation*} H(X) = -\sum_{x \in \mathcal{X}} p(x) \log p(x) \end{equation*}
Knowledge as Computability
Knowledge is related to computational difficulty
- Suppose Alice and Bob know Alice’s public key
- Alice sends her private key to Bob
- Bob has not gained new information (in the information-theoretic sense)
- But Bob now knows a quantity he could not have calculated by himself
Identical Distribution = Identical Knowledge
- Suppose Alice tosses a fair coin and sends the outcome to Bob
- Bob gains one bit of information (in the information-theoretic sense)
- We say Bob has not gained any knowledge as he could have tossed a coin himself
Existence of Simulator = ZK
The prover is trying to prove a statement without leaking knowledge
The set of messages exchanged by the prover and verifier is called a transcript
An interactive protocol is ZK if there is a PPT simulator who can simulate the transcript
Simulation = Generation of identically distributed transcript without knowledge of prover’s secret
Distributions can also be negligibly different
Modeling Statements
A language is a subset of \{0,1\}^*
A prover is interested proving membership of a public value in a language
Examples of languages
- Set of pairs of non-isomorphic graphs G_1, G_2
- \mathcal{QR}_N for a composite N
- \mathcal{QNR}_N for a composite N
Modeling the Prover and Verifier
Prover and verifier will be modeled as algorithms
- Verifier is assumed to be PPT
- Prover may or may not be PPT
Prover is attempting to prove a statement
Malicious or dishonest provers will try convincing the verifier that incorrect statements are true
When the prover is forced to be PPT, we get an argument (not a proof)
Interactive Proof Systems
Let \langle A, B \rangle(x) denote the output of B when interacting with A on common input x
Output 1 is interpreted as “accept” and 0 is interpreted as “reject”
Definition: A pair of interactive machines (P, V) is called an interactive proof system for a language L if V is PPT and the following conditions hold:
- Completeness: For every x \in L, we have \Pr\left[ \langle P, V \rangle(x) = 1 \right] \geq \frac{2}{3}
- Soundness: For every x \notin L and every interactive machine B, we have \Pr\left[ \langle B, V \rangle(x) = 1 \right] \leq \frac{1}{3}
Soundness condition \rightarrow any possible prover
Completeness condition \rightarrow only prescribed prover
By repeating interaction and taking majority, probabilities can be made close to 1 and 0
The \frac{2}{3} and \frac{1}{3} are arbitrary choices by convention
Any c(n), s(n) such that the acceptance gap c(|x|) - s(|x|) \ge \frac{1}{p(|x|)} for a polynomial p will do
Let c,s: \mathbb{N} \to \mathbb{R} be functions satisfying c(n) > s(n) + \frac{1}{p(n)} for some polynomial p(\cdot).
Definition: A pair of interactive machines (P, V) is called an interactive proof system for a language L if V is PPT and the following conditions hold:
- Completeness: For every x \in L, we have \Pr\left[ \langle P, V \rangle(x) = 1 \right] \geq c(|x|)
- Soundness: For every x \notin L and every interactive machine B, we have \Pr\left[ \langle B, V \rangle(x) = 1 \right] \leq s(|x|)
Interactive Proof Example
Suppose Peggy claims that Pepsi in large bottles tastes different than Pepsi in small bottles
Victor challenges Peggy to prove her claim
- Victor asks Peggy to leave the room
- He selects either a large bottle or a small bottle randomly and pours some Pepsi into a glass
- Peggy is called into the room and asked to tell which bottle the Pepsi came from by tasting it
- Victor accepts if Peggy answers correctly
If the claim is correct, \Pr\left[ \langle P, V \rangle(x) = 1 \right] = 1
If the claim is wrong, \Pr\left[ \langle P, V \rangle(x) = 1 \right] = \frac{1}{2} for any P
The acceptance gap is 1- \frac{1}{2} = \frac{1}{2}
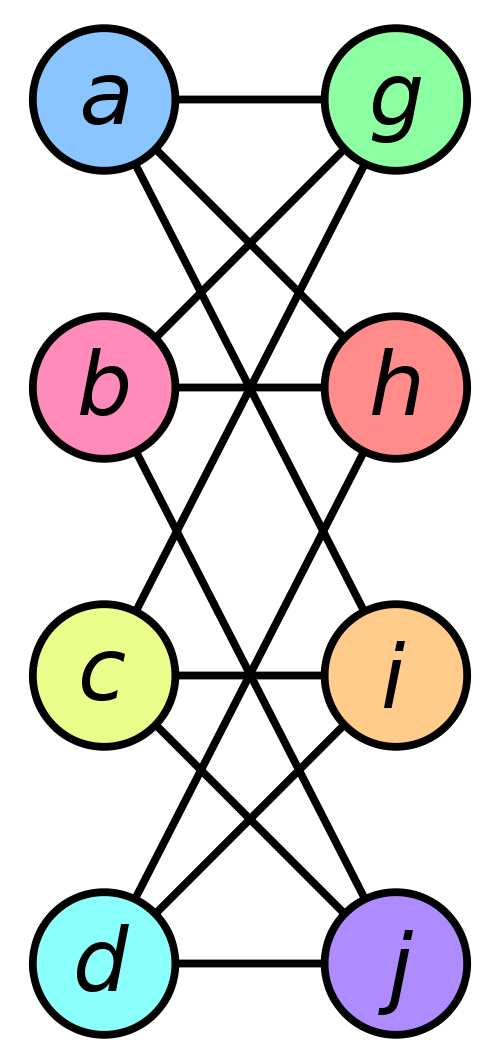
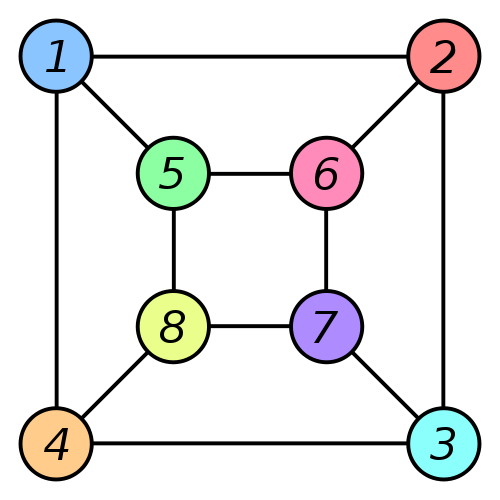
Graph Isomorphism
Graphs G_1 = (V_1, E_1) and G_2 = (V_2, E_2) are isomorphic if there exists a bijection \pi : V_1 \mapsto V_2 such that (u,v) \in E_1 \iff (\pi(u), \pi(v)) \in E_2
Example
Proving Graph Isomorphism and Non-Isomorphism
Proving that two graphs G_1, G_2 are isomorphic is easy
- Prover can send an isomorphism \pi
- Verifier is polynomial-time
How can we prove that two graphs G_1, G_2 are non-isomorphic?
- Checking all bijections \implies exponential-time verifier
Interactive Proof for Graph Non-Isomorphism
Verifier picks \sigma \in \{1,2\} randomly and a random permutation \pi from the set of all permutations over V_\sigma
Verifier calculates F = \left\{ (\pi(u), \pi(v) \mid (u,v) \in E_\sigma \right\} and sends the graph G' = (V_\sigma, F) to prover
Prover finds \tau \in \{1,2\} such that G' is isomorphic to G_\tau and sends \tau to verifier
If \tau = \sigma, verifier accepts claim. Otherwise, it rejects.
Verifier is PPT but no known PPT implementation for prover
- But even an exponential-time prover cannot cheat
If G_1 and G_2 are not isomorphic, then verifier always accepts
If G_1 and G_2 are isomorphic, then verifier rejects with probability \frac{1}{2}
Zero-Knowledge Interactive Proofs
Informal definition: An interactive proof system is zero-knowledge if whatever can be efficiently computed after interaction with P on input x can also be efficiently computed from x (without interaction)
Let \text{view}^P_{V^*}(x) denote the verifier’s view of the protocol
- It is the messages V^* receives and any randomness it generates
Should be possible to generate something with the same distribution as \text{view}^P_{V^*}(x) without interacting with P
Perfect Zero-Knowledge (Ideal)
Formal definition (ideal) : We say (P,V) is perfect zero-knowledge if for every PPT interactive machine V^* there exists a PPT algorithm M^* such that for every x \in L the random variables \text{view}^P_{V^*}(x) and M^*(x) are identically distributed
- M^* is called a simulator for the interaction of V^* with P
Unfortunately, the above definition is too strict
Perfect Zero-Knowledge
Definition: We say that (P,V) is perfect zero-knowledge if for every PPT interactive machine V^* there exists a PPT algorithm M^* such that for every x \in L the following two conditions hold:
- With probability at most \frac{1}{2}, algorithm M^* outputs a special symbol \perp
- Let m^*(x) be the random variable describing the distribution of M^*(x) conditioned on M^*(x) \neq \perp. Then the random variables \text{view}^P_{V^*}(x) and m^*(x) are identically distributed
What if the simulator fails?
The simulator fails with probability at most \frac{1}{2}
It can be run repeatedly until it generates the non-failure output
On the average it requires two runs
HVZK Proof of Graph Non-Isomorphism
Verifier picks \sigma \in \{1,2\} randomly and a random permutation \pi from the set of all permutations over V_\sigma
Verifier calculates F = \left\{ (\pi(u), \pi(v) \mid (u,v) \in E_\sigma \right\} and sends the graph G' = (V_\sigma, F) to prover
Prover finds \tau \in \{1,2\} such that G' is isomorphic to G_\tau and sends \tau to verifier
\text{view}^P_{V^*} = (\sigma, \pi, G', \tau) where G' = \pi(G_\sigma) and \tau = \sigma
A simulator M^* can pick \sigma and \pi randomly, set \tau=\sigma, and set G' = \pi(G_\sigma)
- HVZK = Honest Verifier Zero-Knowledge
- This protocol is only ZK when the verifier follows the protocol honestly
- Suppose there is a third graph G_3 which the verifier wants to check for isomorphism with G_1 or G_2
- The verifier can set G' = G_3 and use the prover’s response to gain knowledge it could not have calculated by itself
- See this note for a ZK protocol
ZK Proof of Graph Isomorphism
- Two graphs G_1 = (V_1, E_1) and G_2 = (V_2, E_2) are isomorphic
- Prover wants to prove that they are isomorphic without revealing the isomorphism \phi: G_1 \mapsto G_2
- Prover picks a random permutation \pi from the set of permutations of V_2
- Prover calculates F = \left\{ (\pi(u), \pi(v) \mid (u,v) \in E_2 \right\} and sends the graph G' = (V_2, F) to verifier
- Verifier picks \sigma \in \{1,2\} randomly and sends it to prover
- If \sigma = 2, then prover sends \pi to the verifier. Otherwise, it sends \pi \circ \phi to the verifier where \left(\pi \circ \phi\right)(v) is defined as \pi\left( \phi(v) \right)
- If the received mapping is an isomorphism between G_\sigma and G', the verifier accepts. Otherwise, it rejects
Verifier is PPT
If \phi is known, prover is PPT
If G_1 and G_2 are isomorphic, then verifier always accepts
If G_1 and G_2 are not isomorphic, then verifier accepts with probability \frac{1}{2}
For an arbitrary PPT verifier V^*, \text{view}^P_{V^*}(x) = \langle G', \sigma, \psi \rangle where \psi is an isomorphism between G_\sigma and G'
The simulator M^* uses V^* as a subroutine
On input (G_1, G_2), simulator randomly picks \tau \in \{1,2\} and generates a random isomorphic copy G'' of G_\tau
- Note that G'' is identically distributed to G'
Simulator gives G'' to V^* and receives \sigma \in \{1,2\} from it
- V^* is asking for an isomorphism from G_\sigma to G''
If \sigma = \tau, then the simulator can provide the isomorphism \pi : G_\tau \mapsto G''
If \sigma \neq \tau, then the simulator outputs \perp
If the simulator does not output \perp, then \langle G'', \tau, \pi \rangle is identically distributed to \langle G', \sigma, \psi \rangle
ZK Proof for Quadratic Residuosity
For N=pq, prover wants to prove x \in \mathcal{QR}_N
Prover knows w \in \mathbb{Z}_N^* such that x=w^2 \bmod N
Verifier does not know factorization of N
Prover does not want to reveal w to the verifier
P picks r \xleftarrow{\$} \mathbb{Z}_N^* and sends y=r^2 to V
V picks a bit b \xleftarrow{\$} \{0,1\} and sends b to P
If b=0, P sends z = r. If b=1, P sends z = wr
If b=0, V checks z^2 = y. If b=1, V checks z^2 = xy
For an arbitrary PPT verifier V^*, \text{view}^P_{V^*}(x) = \langle y, b, z \rangle where z^2 = x^by
Consider a simulator M^* which does the following
- M^* picks z \xleftarrow{\$} \mathbb{Z}_N^* and b \xleftarrow{\$} \{0,1\}
- M^* sets y = \frac{z^2}{x^b}
- If V^*(y) = b, then M^* outputs \langle y, b, z \rangle. Otherwise, M^* outputs \perp
Interactive Proof for Quadratic Non-Residuosity
- For N=pq, prover wants to prove x \in \mathcal{QNR}^{+1}_N
- Verifier does not know factorization of N
- How can P prove x is a quadratic non-residue without revealing the factorization of N?
- V picks y \xleftarrow{\$} \mathbb{Z}_N^* and a bit b \xleftarrow{\$} \{0,1\}
- If b=0, V sends z = y^2. If b=1, V sends z = xy^2
- If z \in \mathcal{QR}_N, P sends b'=0.
- If z \in \mathcal{QNR}_N^{+1}, P sends b'=1
- V accepts if b'=b
The above protocol is honest verifier zero-knowledge (HVZK) but not ZK
Consider a PPT verifier V^* which wants to find out if some u \in \mathbb{Z}_N^* is in \mathcal{QR}_N
By replacing x in the above protocol with u, verifier V^* can get information about u
If the protocol was ZK, then there exists a PPT M^* which can get the same information without interacting with P
This contradicts the non-existence of PPT algorithms for checking membership in \mathcal{QR}_N
- Solution: V has to prove that it either knows the square root of z or zx^{-1} to P
- The number of interaction rounds increases from 2 to 4
ZK Proof for Quadratic Non-Residuosity
P wants to prove that x \in \mathcal{QNR}_N^{+1} for N=pq
V picks y \xleftarrow{\$} \mathbb{Z}_N^* and a bit b \xleftarrow{\$} \{0,1\}
If b=0, V sends z = y^2. If b=1, V sends z = xy^2
For 1 \le j \le m,
V picks r_{j,1}, r_{j,2} \xleftarrow{\$} \mathbb{Z}_N^* and \text{bit}_j \xleftarrow{\$} \{0,1\}
V computes \alpha_j = r_{j,1}^2 and \beta_j = xr_{j,2}^2.
If \text{bit}_j = 0, V sends \text{pair}_j = (\alpha_j, \beta_j).
If \text{bit}_j = 1, V sends \text{pair}_j = (\beta_j, \alpha_j).
- P sends V a bit string \left[ i_1, i_2,\ldots,i_m \right]\in \{0,1\}^m
V sends P the sequence v_1, v_2,\ldots,v_m
- If i_j = 0, then v_j = (r_{j,1}, r_{j,2}).
- If i_j = 1, then v_j = yr_{j,1} if b=0. So V sends a square root of z\alpha_j
- If i_j = 1, then v_j = xyr_{j,2} if b=1. So V sends a square root of z\beta_j
P checks the following:
- If i_j=0, P checks if (r_{j,1}^2, r_{j,2}^2x) equals \text{pair}_j, possibly with elements in the pair interchanged.
- If i_j=1, P checks if v_j^2z^{-1} is a member of \text{pair}_j.
If z \in \mathcal{QR}_N, P sends b'=0.
If z \in \mathcal{QNR}_N^{+1}, P sends b'=1
V accepts if b'=b
Further reading
- Sections 4.1, 4.2, 4.3 of Foundations of Cryptography, Volume I by Oded Goldreich
- The Knowledge Complexity of Interactive Proof Systems, S. Goldwasser, S. Micali, C. Rackoff, 1989. https://doi.org/10.1137/0218012
- Alon Rosen’s lecture in the 9th BIU Winter School on Cryptography. video